Information Security Data Flow Diagram Cyber Security Isomet
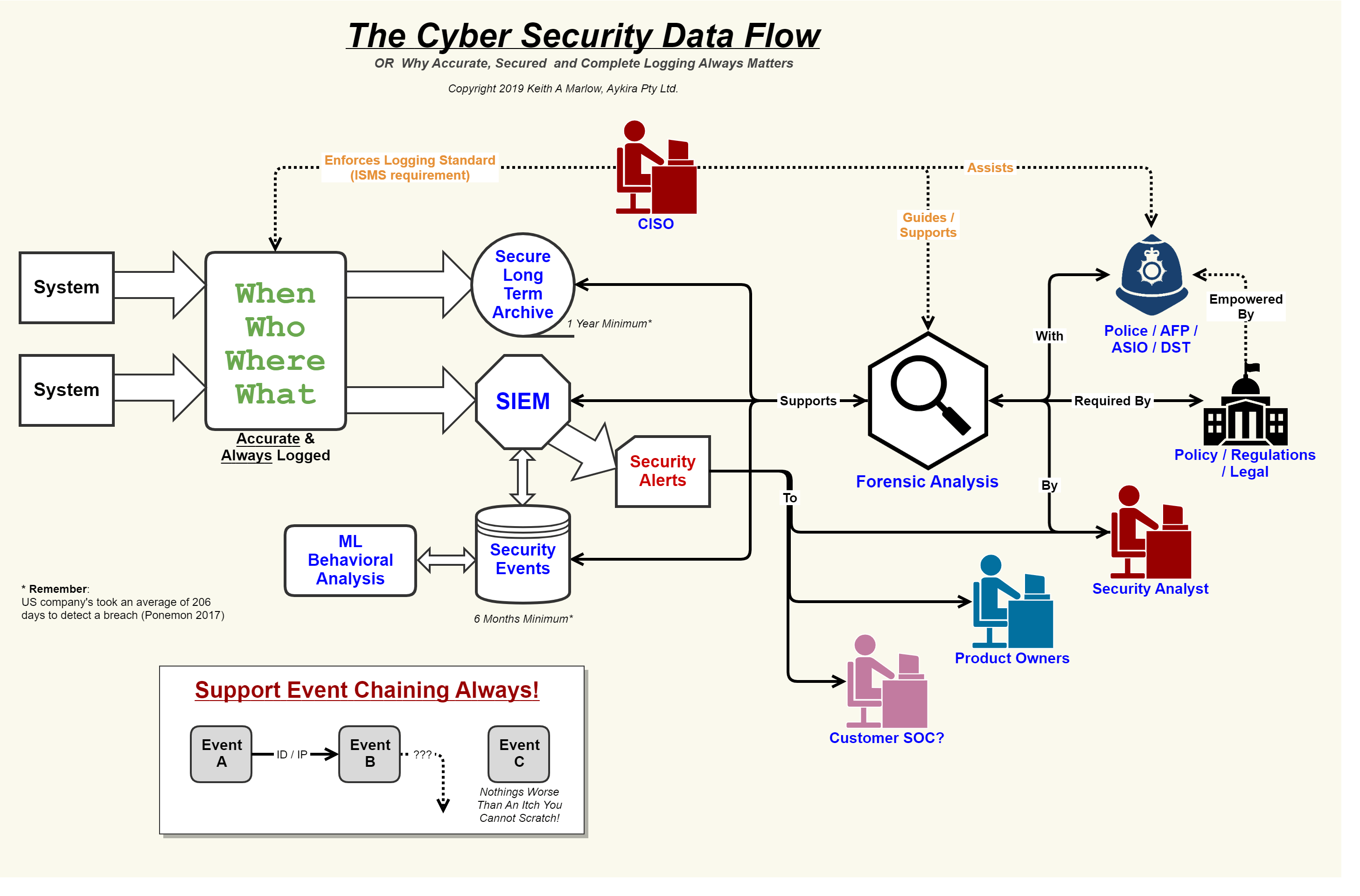
Cyber security isometric flowchart royalty free vector image Security event logging, why it is so important – aykira internet solutions Data flow diagram showing how data from various sources flows through
Data Flow Diagram Security - Management - Ppt Information Framework
Data flow diagram of smart security framework Data flow diagram in software engineering Data flow and security overview
Database design tool
Membuat data flow diagramNetwork security model Data flow diagramSecurity event logging, why it is so important – aykira internet solutions.
Network security diagrams solutionA beginner's guide to data flow diagrams Diagram dfd flow data conceptdraw system management symbols pro create using draw information diagrams example accounting flowchart systemsNetwork security architecture diagram.

Security network diagram control computer diagrams devices networks secure access encryption solution cloud examples model architecture example conceptdraw software system
Data flow diagram securityNetwork security model Flow diagram data physical online types symbols lucidchart click tips marketingPhysical flow diagram data database lucidchart tool template dfd example software examples marketing templates.
Accounting information systems flowchart symbolsCyber security plan template Security network diagram model cloud diagrams government computer solution devices conceptdraw access example networks architecture cybersecurity solutions information models examplesIot & enterprise cybersecurity.

Data flow diagram examples symbols, types, and tips
Architecture cybersecurity enterprise iot cyber security diagram system softwareYour guide to fedramp diagrams [diagram] process flow diagram vs data flow diagramData flow diagram.
Data flow diagram templates to map data flowsNetwork security diagrams Security network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructureMicrosoft graph security api data flow.

Security flow data cyber event logging diagram internet logs important why so together showing concerning events au putting
Security flow cyber data event logging diagram logs internet important why so together putting events auFlow dfd flows creately business atm Data flow diagram.
.